Default Passwords Strike Again – This Time On Air
Breaking into broadcast transmissions isn’t anything new. We can go back to 1977 and the interruption of Southern Television, replacing the audio feed with some “interesting” content.
Doing similar nowadays, where digital studio to transmitter links (STL) reign supreme, is much harder. How do you break into an encrypted 5Ghz radio link or dig into a telco provisioned IP circuit?
Well, turns out you don’t need to. And no, I’m not talking about analogue FM links you see on 1.5Ghz as favoured by some community radio stations. Nor am I talking about overpowering a re-broadcast link. Seriously, there are FM transmitters out there that could be taken over with a relatively low power transmission of your own, overpowering the distant signal it’s setup to rebroadcast. I’m not going to reveal where any of those are (if I know about them) and it’s not exactly legal either!
That said, taking over the output of some US radio stations doesn’t even require you to leave your house. Turns out they’d been using the Barix Instreamer/Exstreamer solution for carrying audio between their studios and the remote transmitters.
Now, that isn’t usually a problem. I know a few places where this kit is deployed here in the UK. It’s usually on a restricted and monitored IP networks with the endpoints in secured locations. You’d have to do some serious work to get at the kit, though these things are never impossible.
It appears, based on an advisory sent out by the Michigan Association of Broadcasters, and news stories from the likes of Ars Technica that such precautions weren’t taken. Some surprisingly graphic content ended up on air as the Barix kit was re-configued to pull an entirely different stream. Oh, and the management password was changed to prevent the settings being changed back.
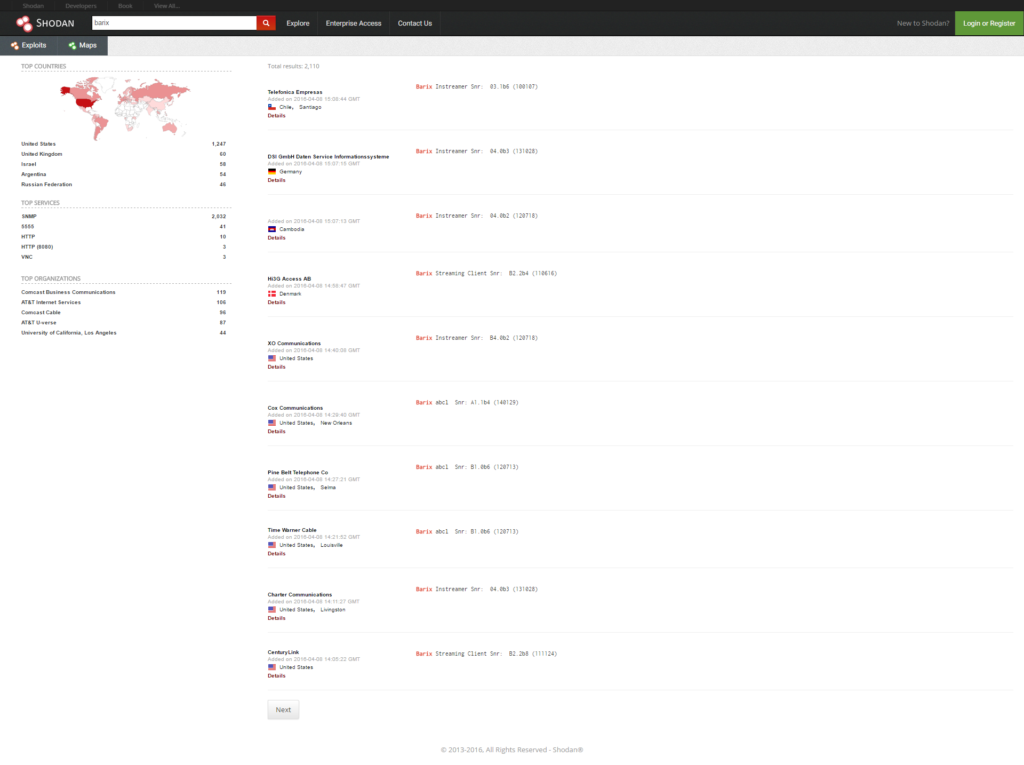
That’s rather embarrassing so what happened? Firstly, it looks like Shodan, a search engine for finding almost anything connected to the Internet was used to find the boxes.
If you’ve never come across Shodan before, it’s a surprisingly powerful tool. It’ll help you locate everything from baby monitors and webcams to unprotected database servers for websites. If you’ve got anything connected to the Internet, it’ll likely show up in there. In fact, a quick search I did myself for “barix” turns up a surprising number of results.
Now admittedly, not all of those results are going to be Barix Instreamer/Exstreamer boxes. However, it does show how exposing anything directly to the Internet can open it up to abuse. In fact, anyone that’s put an SSH server out in the wild knows that you’ll see constant dictionary attacks. That’s the reason you take time to secure the server properly and invest in proper firewalls, IDS/IPS and monitoring.
On a side note, I used to consider a guy that installed Tripwire, a tool that alerted you to any system file change, on every server a little paranoid. Doesn’t seem quite such a bad thing now!
Anyway, the fact management interfaces of a lot of these devices is directly exposed to the world is generally considered a bad thing. I’ll admit, properly installing and managing a VPN on a remote site can be complicated but it’s far less embarrassing than what went out on air in this case.
The other big issue is the most shocking. I can almost understand exposing the management interface to the world. Well, not really but I’m sure someone will have a justification. However, there’s no justification for leaving the password as the out of the box default.
Seriously, that’s the general consensus on how the boxes were gotten in to and configuration changed. It’s understood that there were dictionary attack attempts against some of the compromised boxes and that’s unfortunately one of the attacks you’ll regularly see on the Internet. But that doesn’t explain why these things are deployed with default settings.
I guess this is yet another lesson how it’s the real basic attacks that will get the results. That combined with some research I saw recently detailing how people will plug USB pendrives they find in the car park into their computers, is a reminder that we still need to keep on top of the basics.
While the attack techniques used in this case are as old as the hills, I really do believe we’ll see more of this sort of thing. Not necessarily changing the content of radio stations but the expansion of IoT devices getting into the real world with minimal security built-in makes them easy targets. Blaming the people that deploy the devices is easy and in this case, simple measures should have been taken.
There will always be weak points in any system, IT or broadcast. Keeping on top of securing these is continually becoming more important.